
Key Insights:
- Effective CDD processes are essential in the crypto business for identifying and verifying customer identities.
- Regular monitoring is fundamental for spotting suspicious activities in customer transactions.
- Compliance with the so-called Travel Rule is vital for maintaining transaction transparency and fulfilling regulatory requirements.
- Various red flags, such as transaction sizes and patterns, can signal potential illicit activities in crypto transactions.
In Part 1 of our extensive FATF 101 guidance, we focused on the main definitions of virtual assets (VAs) and virtual asset service providers (VASPs) and explained the difficulties in applying FATF recommendations to the P2P platforms and DeFi.
This part of our exploration into FATF compliance takes a more hands-on approach. We will delve into practical methodologies for implementing these regulations and check real-life examples.
Here are the steps to apply the FATF standards to the crypto business
- Implement effective CDD
Customer Due Diligence (CDD) is a comprehensive process involving customer identification, verification, and ongoing monitoring, all adapted to the level of risk associated with each customer and transaction. To make the procedure effective, VASPs need to:
- Identify customers and verify their identities using reliable sources, such as official documents or information. The necessary data includes the customer’s name, physical address, date of birth, and a unique national identifier number. Additional information like IP addresses, geolocation data, device identifiers, VA wallet addresses, and transaction hashes may also be collected.
- Find the beneficial owner.
- Understand the intended purpose and nature of the customer’s business.
- Continually monitor customer transactions to ensure consistency with their business profile and to spot any suspicious activities.
“Remember these three key points for CDD: 1) Pay extra attention to transactions over $1,000 in USD or EUR. 2) Make sure you know who your customer and the real owner of the funds are, either before or when you start doing business with them. 3) How much you check depends on how risky the customer or the transaction is: more checks for higher risks, fewer for lower risks.”
Josh Martin
- Continually monitor customer transactions to identify suspicious ones
VASPs need to regularly check their transactions to ensure they match what they know about their customers and business dealings. This monitoring process also involves spotting any changes in how customers behave or in their personal details. Depending on the risk level and each customer’s specific situation, VASPs should adjust how closely they monitor these aspects.
For instance, if transactions involving unhosted wallets are considered high-risk, VASPs might choose to watch these transactions more closely.
Modern automated systems can flag unusual patterns that might indicate money laundering or other illicit activities.
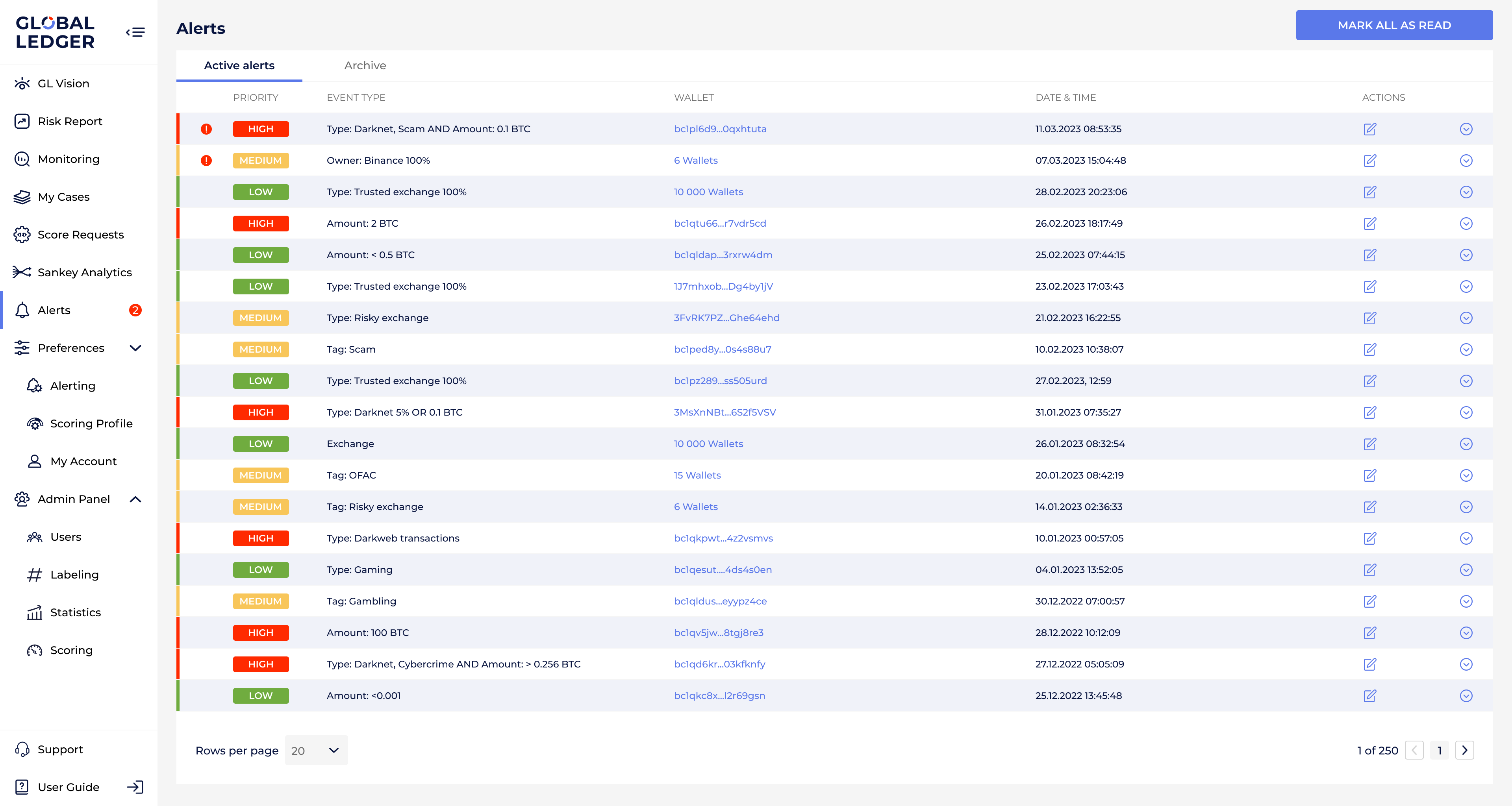
GL screenshot with active alerts, their priority, event type, date, time, and wallet they are associated with
- Follow the Travel Rule
The rule requires businesses to know and record who is sending and receiving the money in all crypto transactions. They must also keep an eye on these transactions to catch any missing information about the parties involved.
- Check counterparty VASP
When starting a new relationship with another VASP, they should gather specific information about the counterparty mentioned in the CDD and Correspondent banking sections. This may include checking public registries, legal documents, and compliance reports to understand how the counterparty implements AML/CFT controls.
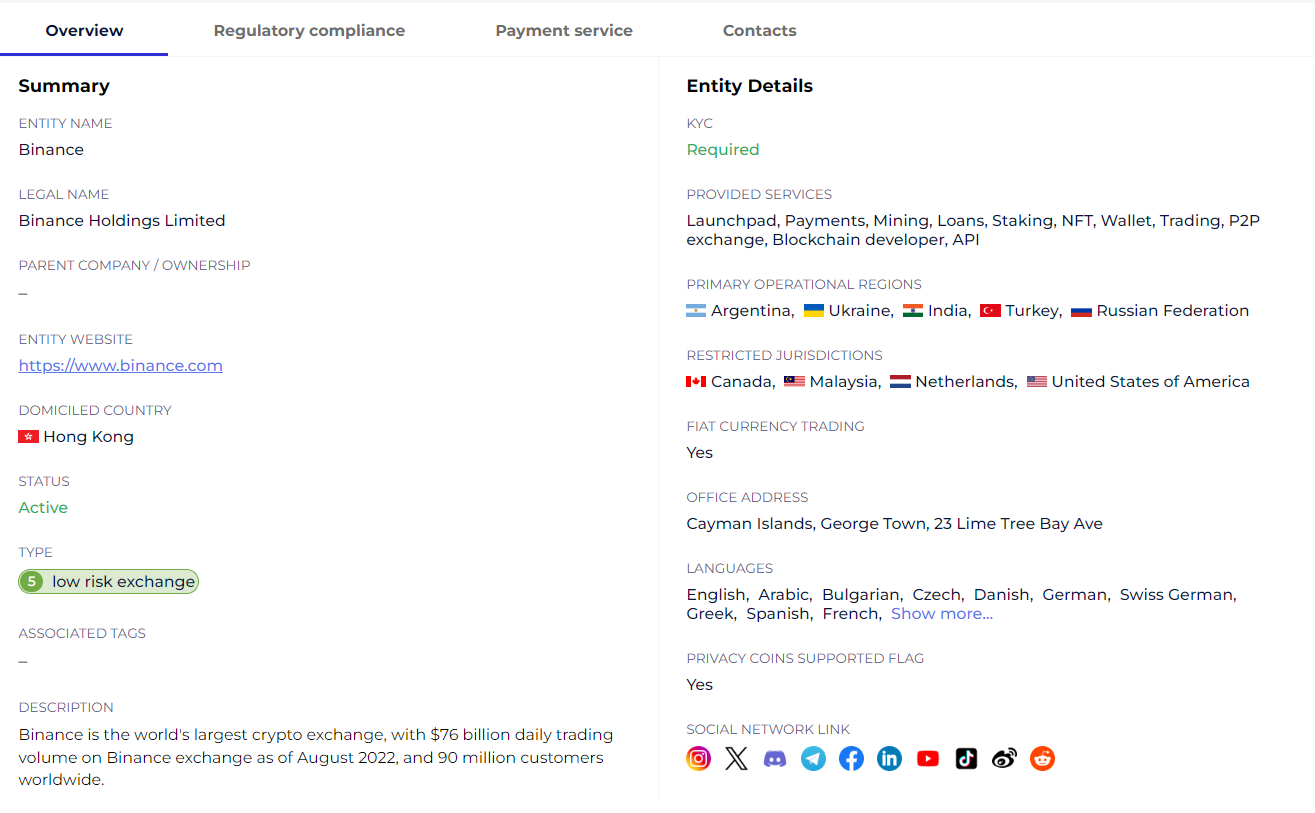
GL screenshot with entity details
- Strengthen internal controls for politically exposed persons
This step involves three main actions:
- Identification to find out if a customer or the beneficial owner of a transaction is a politically exposed person (PEP).
- Risk assessment to understand the potential for money laundering or terrorist financing associated with that PEP.
- Additional measures for high-risk PEPs, such as identifying the PEP’s source of wealth and the source of funds involved in the transaction.
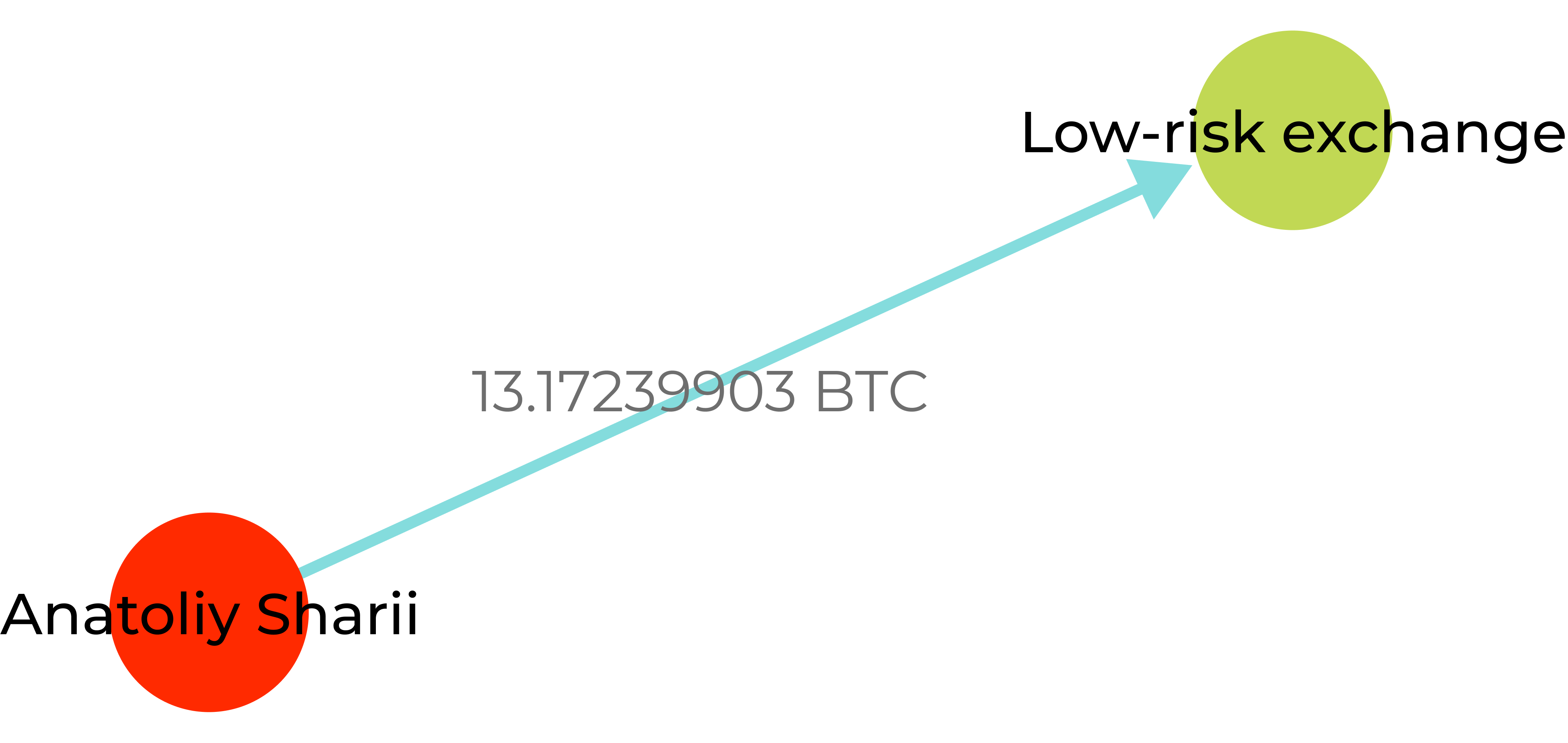
GL screenshot showing a transaction from the address published on the blocked YouTube channel of Russian propagandist Anatoly Shariy—founder of the Party of Shariy banned in Ukraine
How do you understand activities related to crypto are potentially illicit? FATF specifies certain red flags.
These red flags help to identify crypto-related risks
These indicators provide crucial insights for financial institutions, businesses, and regulatory bodies to identify and mitigate illicit activities. They are related to:
- Transactions
Unusual size and frequency of transactions, such as small, structured amounts or multiple high-value transactions in quick succession, often raise suspicion.
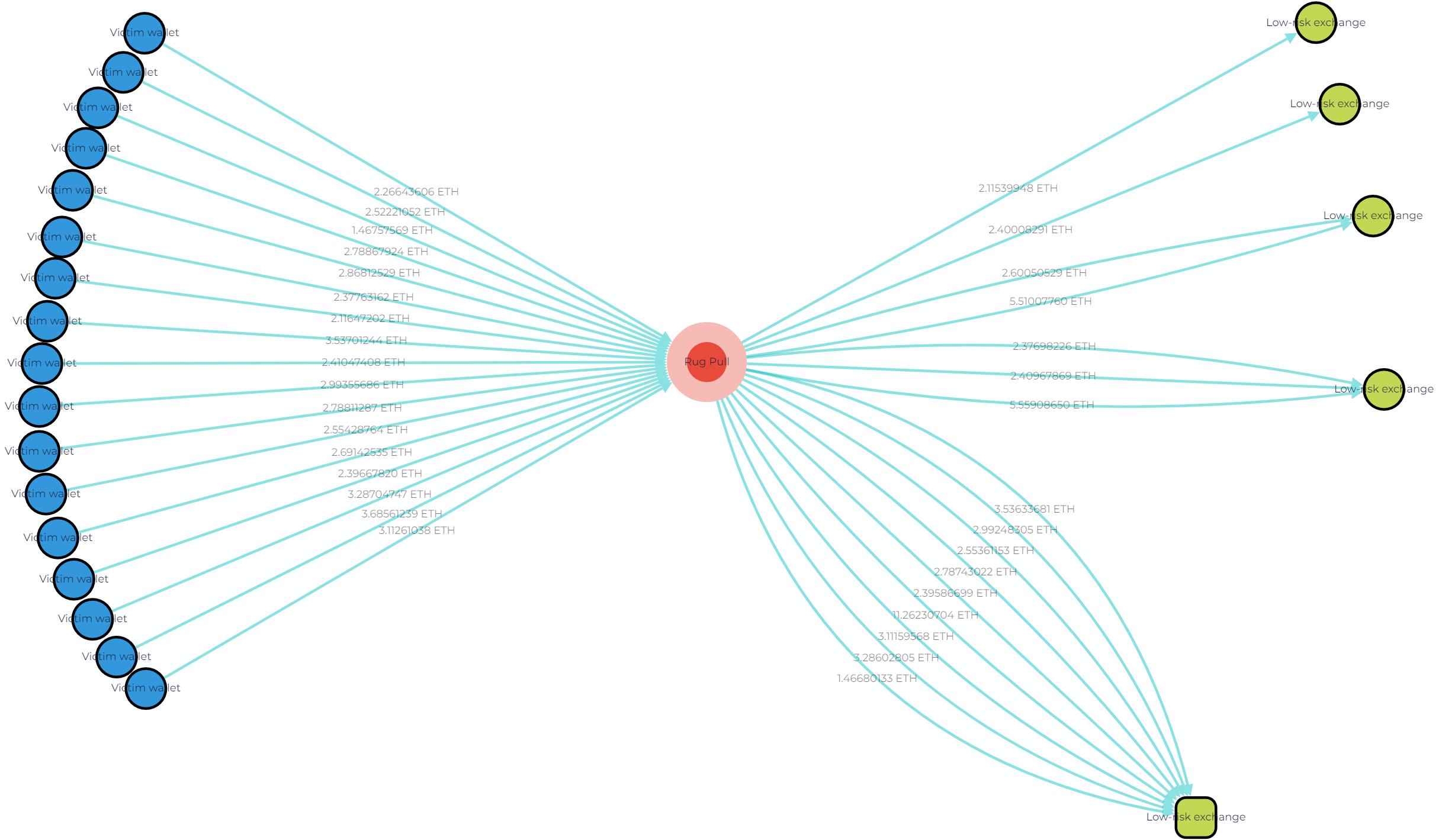
GL Vision screenshot illustrating the flow of funds from meme tokens rug pull to fraudster’s wallet and then to separate low-risk exchange wallets. The funds are moved in small transactions
- Transaction patterns
Irregularities in transaction behaviors, including activities associated with new users making large deposits or sudden influxes of funds without a clear business goal.
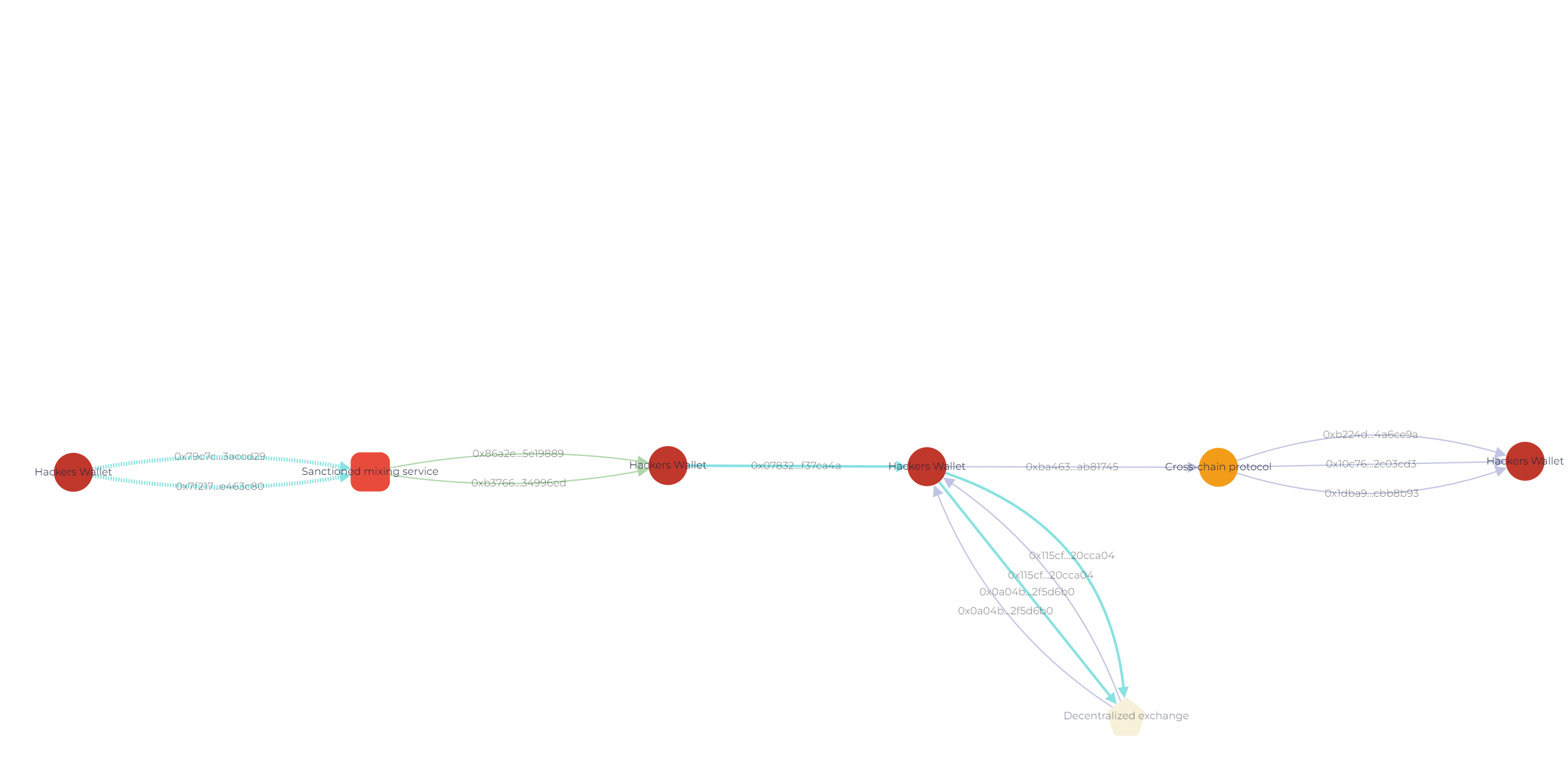
GL Vision screenshot showing the flow of funds to the mixing service. The assets are divided into structured transactions
Moreover, such transactions may even include losses, for example, related to crypto-fiat exchange.
- Anonymity
Transactions that involve a high degree of anonymity, such as the use of privacy coins or transactions through unregistered or unlicensed service providers.
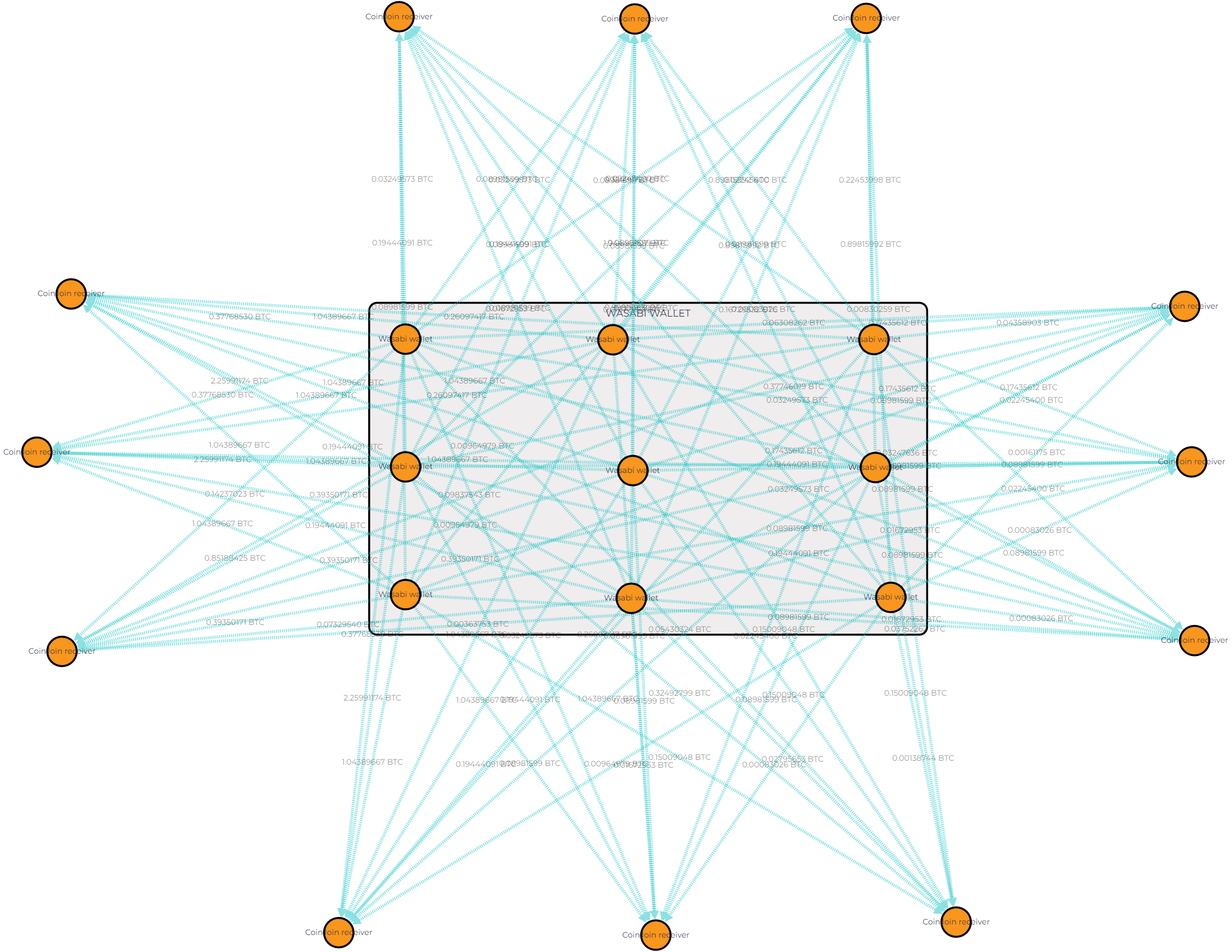
GL Vision screenshot showing transactions via Wasabi Wallet — a privacy-focused wallet. It uses a coinjoin method, which combines multiple Bitcoin transactions into one to enhance privacy and operates over the Tor network for added anonymity
- Sender and recipient
Suspicious activities can also be flagged based on the profiles of senders or recipients. This includes inconsistent information during account creation or KYC processes, transactions from high-risk jurisdictions, creating separate accounts under different names, customers being known to law enforcement due to previous criminal association, and more.
Here’s an example. Lazarus group is on the OFAC sanction list. So, any address connected to it becomes high-risk. Like 0xa0e1c89Ef1a489c9C7dE96311eD5Ce5D32c20E4B added to the list in 2022:
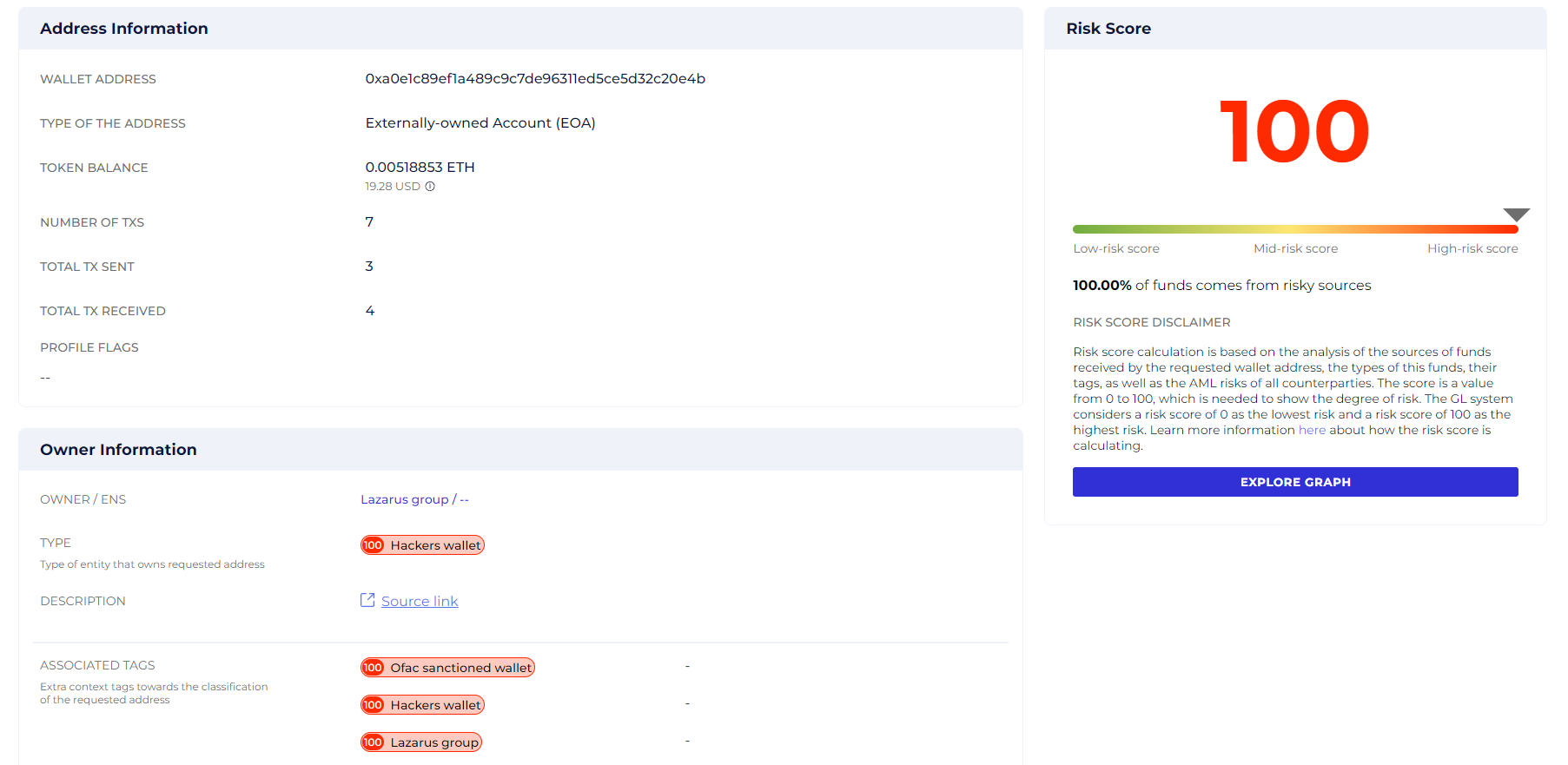
Screenshot from the GL risk report showing risk score of the 0xa0e1c89Ef1a489c9C7dE96311eD5Ce5D32c20E4B address linked to Lazarus group
- Source of funds
Red flags are also raised when the source of funds or wealth for transactions is unclear, suspicious, or inconsistent with the customer’s profile. This can include funds originating from known fraudulent or sanctioned sources, for example, the Hydra darknet marketplace.
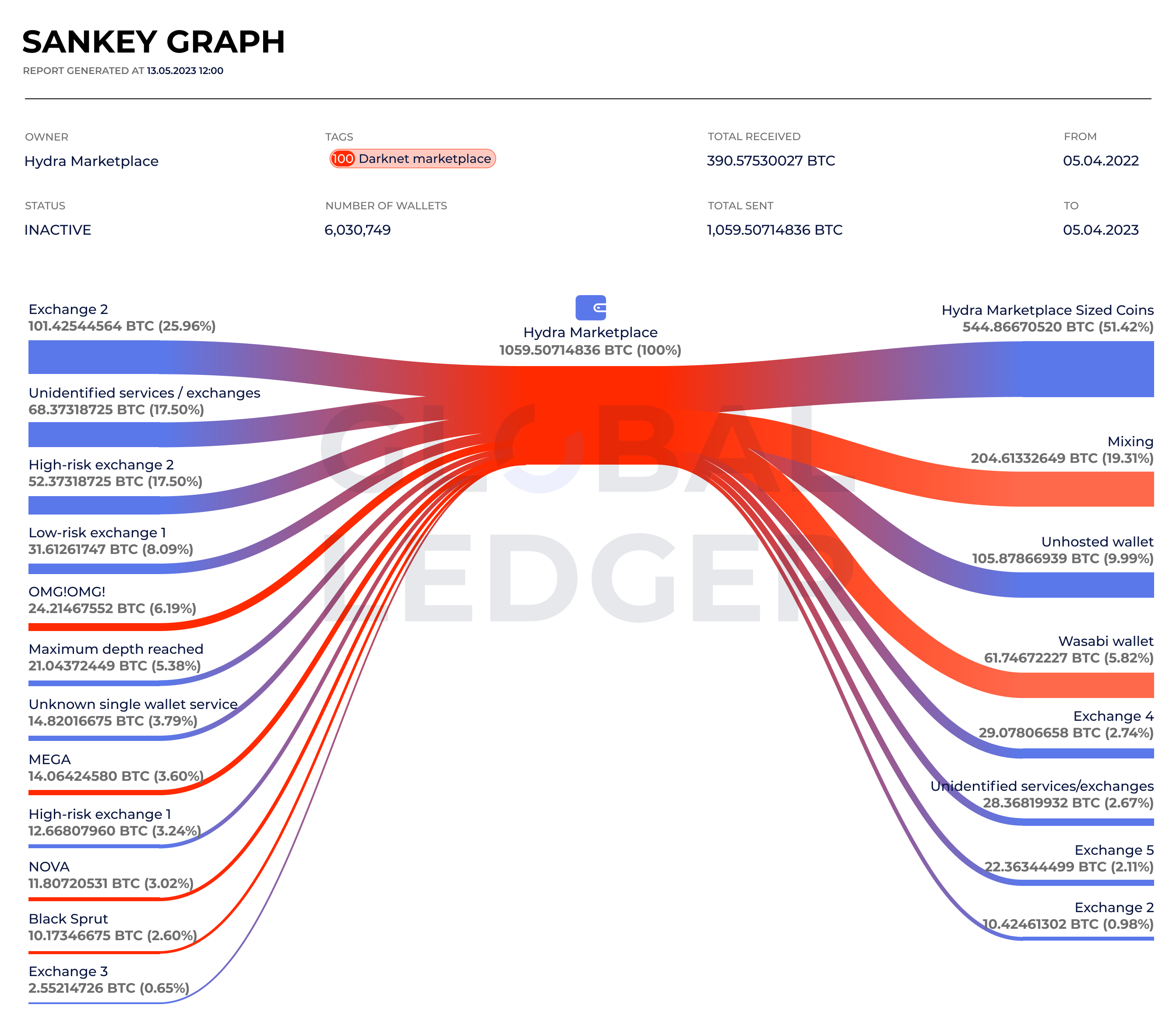
GL Sankey graph illustrating BTC received and withdrawn via Hydra Marketplace wallets from April 5, 2022, to April 5, 2023
- Geography
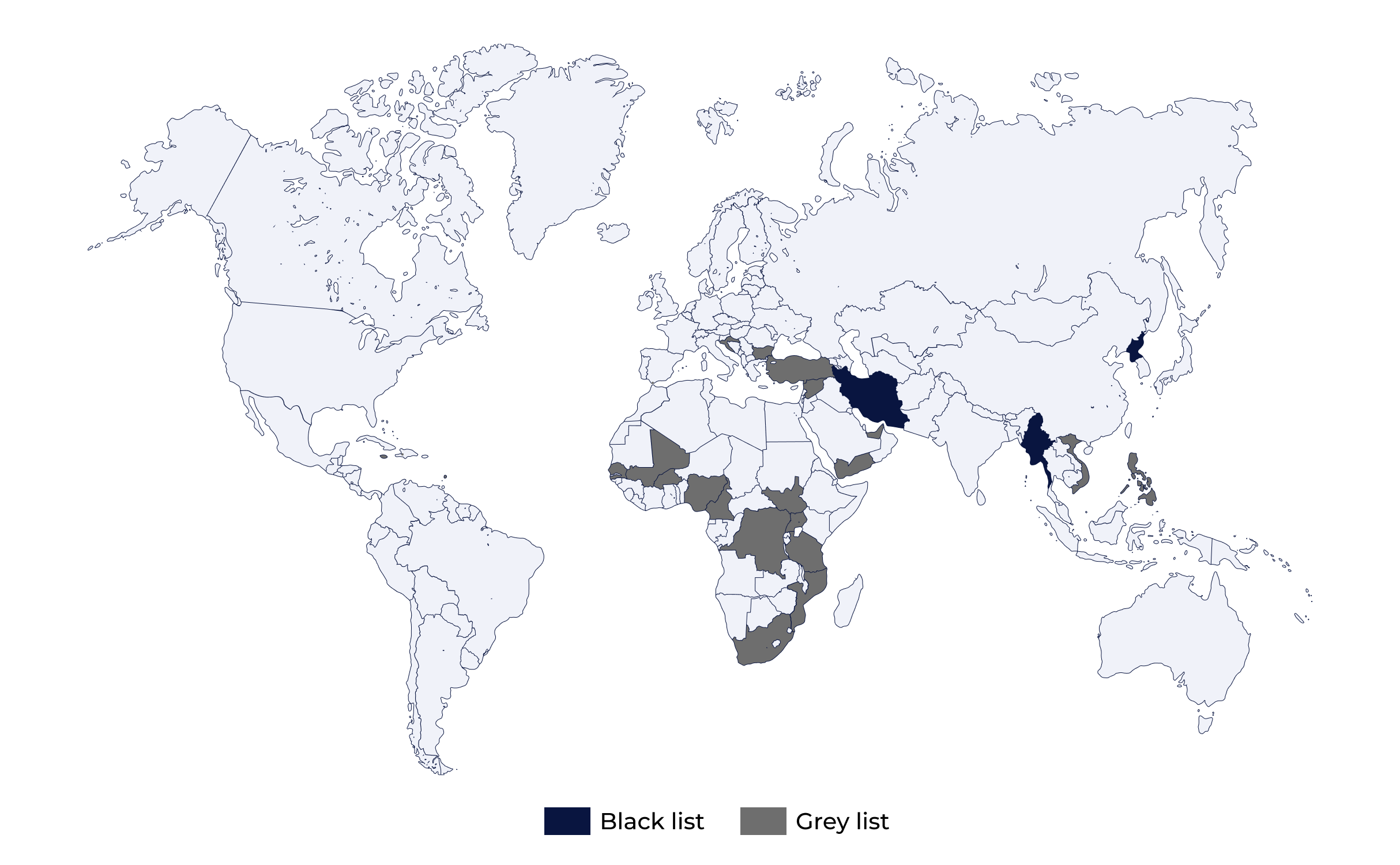
Transactions involving VASPs in jurisdictions with weak or non-existent AML/CFT regulations are often red-flagged, especially when the funds’ origins or destinations do not align logically with the customer’s location or business activities. Risky jurisdictions and those under increased monitoring are specified in FATF black and gray lists.
Let’s follow Josh* as he handles some real-life transaction checks
*Josh Martin is a made-up character who shows us what it’s like for compliance officers trying to follow FATF rules. Through his story, we get a closer look at the real challenges they face , making it easier to grasp the complexities of meeting regulatory requirements.
- Case 1
He is checking the address 16X3…Bi2w (highlighted in black), and everything seems ok:
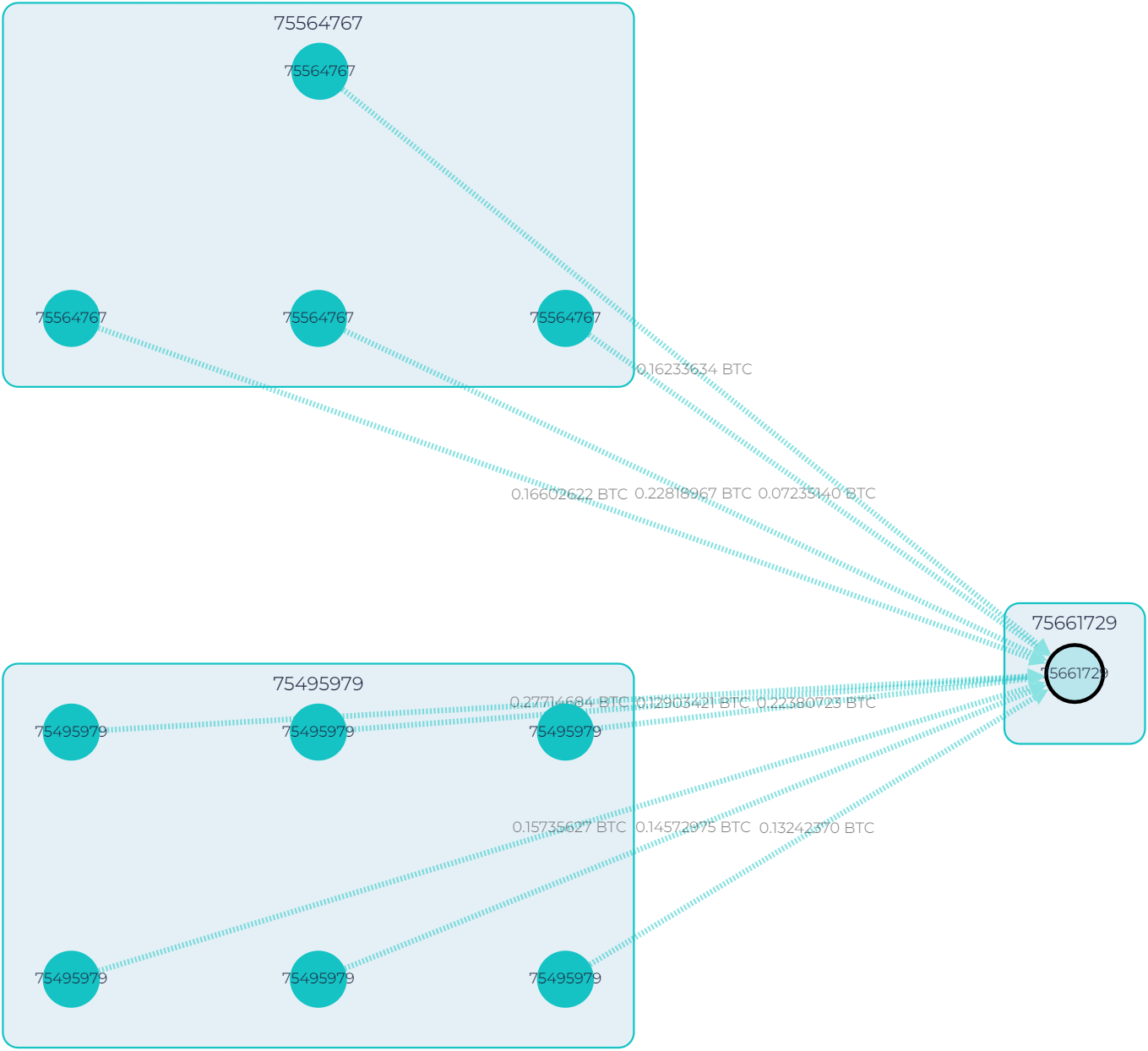
GL graph showing the flow of funds to address 16X3…Bi2w (highlited in the black circle)
But the Source of funds tab shows a risk score of 96. Why?
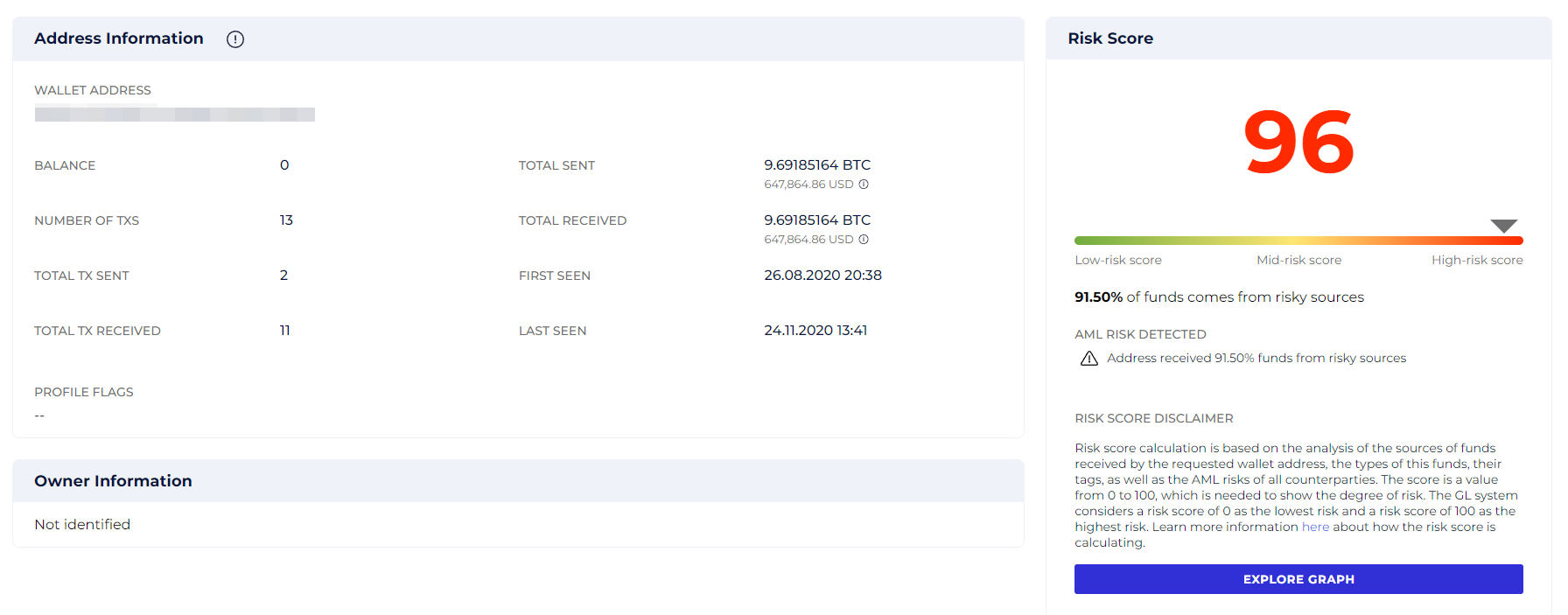
GL risk report for address 16X3…Bi2w showing its risk score
91.4% of funds come from risky sources, and if we trace just a few transactions back, we will see why. The funds came from Blender.io, a sanctioned mixing service.
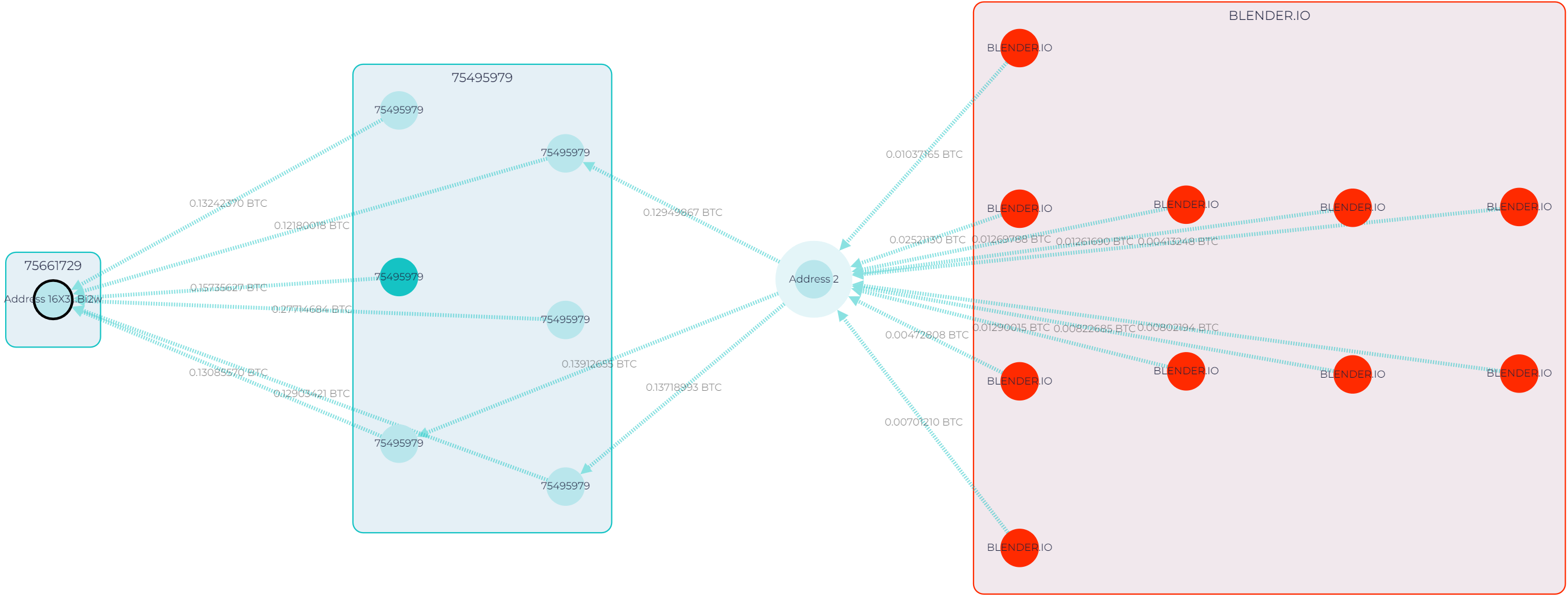
GL graph showing the flow of funds from Blender.io-owned cluster to address 16X3…Bi2w
“OK, this one was easy. Undoubtedly, this transaction and address should be flagged, according to FATF. A sanctioned entity is a 100% risky source.”
Josh Martin
- Case 2
Here, we have an address 34xp…Twseo, with numerous transactions and an impressive balance of 248,500+ BTC.
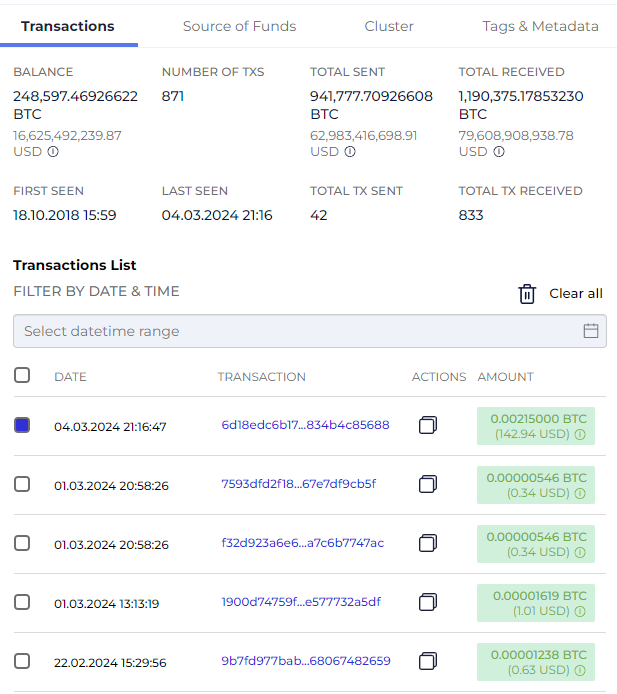
Screenshot from GL showing transactions to address 34xp…Twseo
However, this address has signs of belonging to a crypto service. For example:
- The wallet has a substantial overall fund turnover.
- Transactions conducted by this wallet lack a consistent behavioral pattern.
- The amount of each transaction is relatively small.
“This address looks like it belongs to an exchange. I’d rather not flag it, as there are no signs of illicit activities”
Josh Martin
That’s the right choice because 34xp…Twseo is a cold wallet owned by a low-risk exchange.
Screenshot from GL showing transactions to address 34xp4…Twseo
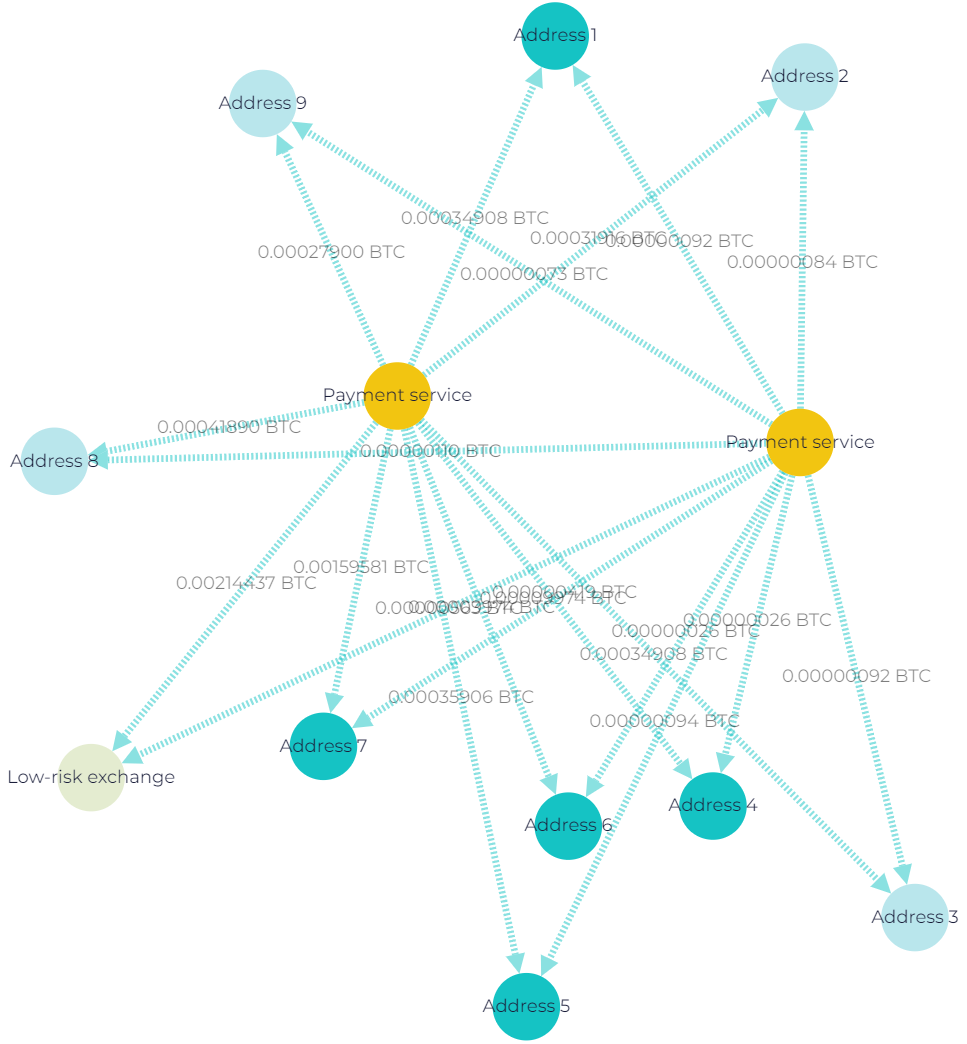
Case 3
In this case, the exchange uses single-use wallets to pay out clients.
- Funds are first transferred to the payout wallet from various internal wallets belonging to the VASP.
- The payout wallet then executes an outgoing transaction, simultaneously distributing the funds to several wallets. This typically includes one VASP wallet and several client wallets.
- The bulk of the funds is then sent to a wallet belonging to another exchange, where the process is repeated.
Screenshot from GL Vision showing customers’ withdrawals via single-use wallets in the Bitcoin network
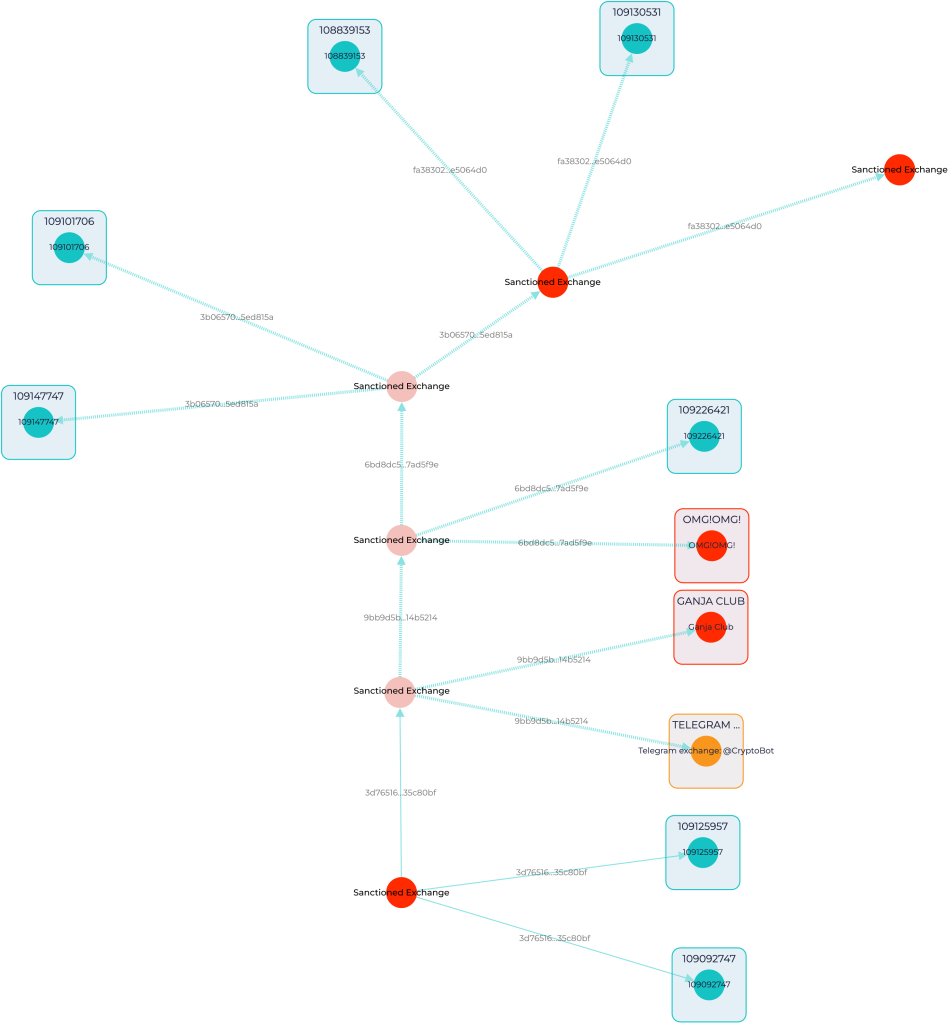
But what’s wrong with the scheme? The sanctioned exchanges employ such a system of single-use wallet chains for their transactions. In this system, each new withdrawal transaction is processed through a different wallet. After the transaction is completed, any remaining funds are then transferred to the next wallet in the chain. This approach ensures that each wallet is used only once before moving on to the next in the sequence.
In contrast, for client withdrawals, major exchanges often use the same wallet that is also utilized for depositing funds.
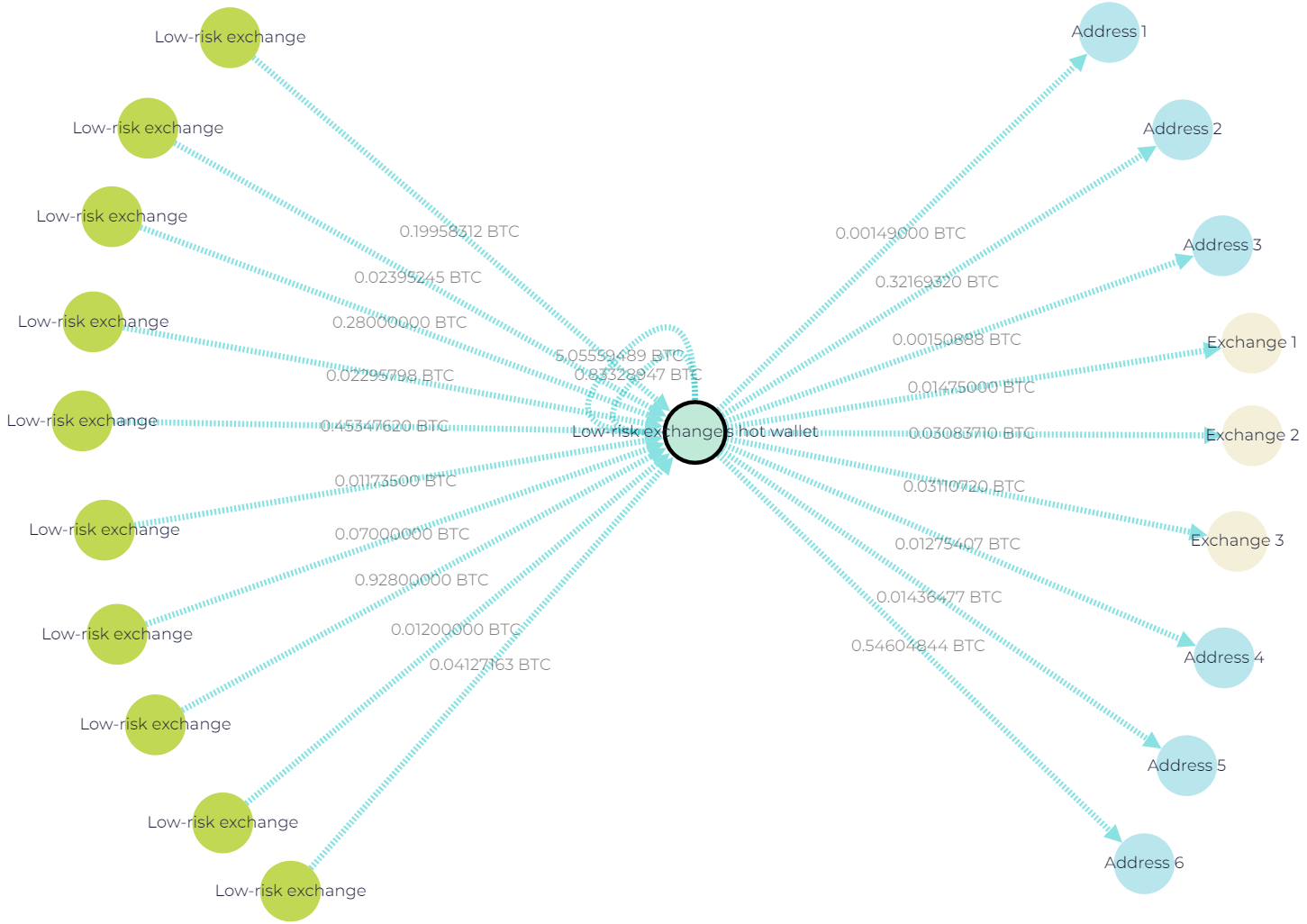
Screenshot from GL showing customer withdrawals from low-risk exchange’s hot wallet on the Bitcoin network
“This might be a tricky case. On the one hand, nothing seems to be wrong with those transactions. But if you dive deeper, you can clearly see a pattern, with single-use wallets and outgoing transactions, simultaneously distributing assets to several wallets. This is suspicious activity, which I would flag.”
Josh Martin
Looking ahead at how FATF guidelines may evolve
We might see stronger international collaboration, with FATF guidelines pushing for a more unified global standard. This would make it harder for bad actors to exploit jurisdictional gaps.
With the growth of the DeFi sector, the organization might develop specific guidelines for these platforms, potentially requiring them to implement identity verification processes similar to traditional financial institutions.
As technology advances, FATF guidelines will likely adapt to address the new ways in which these technologies could be used for financial crime.